Logging in and out i4connected, with an External Provider
Check out this article and learn how to login into the i4connected portal via the Custom OpenID Connect protocol. We prepared this for your own convenience.
The i4connected application gives users the freedom to chose multiple external Identity Providers to sign into the portal. The accepted External providers are:
Facebook
Twitter
Google
Microsoft
Custom OpenID Connect
Tip
For more details about the i4connected External Providers, please also visit the dedicated article here.
Important
PREREQUISITES
An Identity Provider server/account should be available, as you will need to extract some information, in order to enable the possibility to log in with an external provider.
External providers can only be enabled on an HTTPS connection.
Please follow the below-described steps in order to be able to log into i4connected via an External Provider of your choice:
Open your Identity Provider server/account in order to obtain the necessary authentication information.
Tip
Depending on the provider you intend to use, please also check the "Setting up External providers" article in order to learn more details about the expected authentication information
Open the appsetting.json file, available under your i4connected Identity folder, on the machine running the i4connected installation.
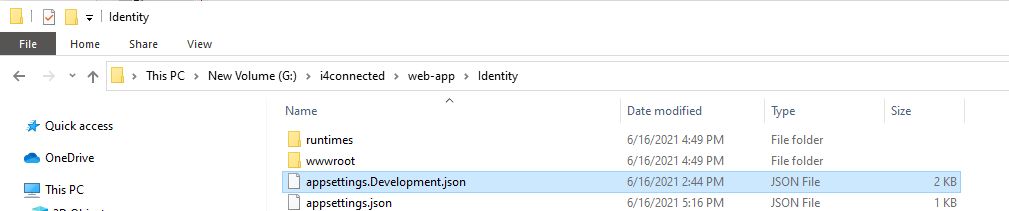
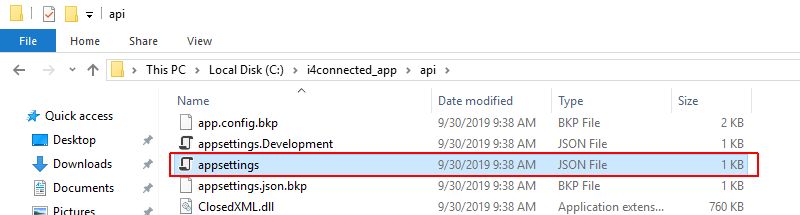
Warning
For the i4connected environment running of versions lower than 5.6.15, the settings for External providers can be found under the API Folder in the appsettings.json file.
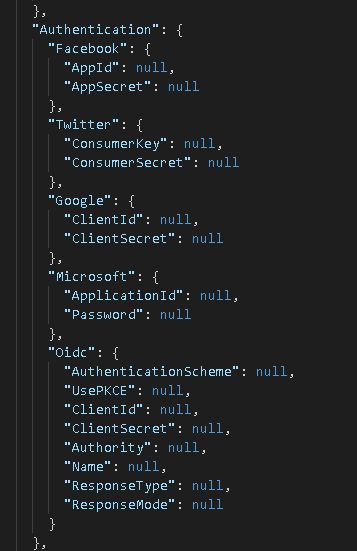
Identify your External provider settings in the Authentication area and start filling in the requested information. The authentication information should be added between double quotes ("...").
Tip
Facebook
AppId - The unique identification number of your Facebook application account.
AppSecret - The secret key of your Facebook application account.
Twitter
ConsumerKey - The unique identification key of your Twitter application account.
ConsumerSecret - The secret key of your Twitter application account.
Google
ClientId - The unique number used to identify your Google account.
ClientSecret -The secret key of your Google account.
Microsoft
ApplicationId - The unique identification number of your Microsoft application.
Password - The Client secret (application password) consisting of a secret string that the application uses to prove its identity when requesting a token.
Custom OpenID Connect
AuthenticationScheme - The scheme used for external sign-out. To enable the external sign-out scheme for the OIDC provider, the user needs to define a scheme, otherwise, the default value will be used and the external sign-out will be disabled.
ClientId - The unique number of the client for which all tokens must be issued.
ClientSecret - The secret key of the client.
Authority - The URL of the external identity provider/server.
Name - The name of the client that will be displayed in the application.
ResponseType - The type of response can be: none, code, token, id_token, or a combination of the last three options.
ResponseMode - The mode of the response can be: query, fragment, or form_post.
MetadataAddress - Optionally, allows the user to set a discovery endpoint address for obtaining metadata.
Scopes - Optionally, allows the user to list additional permissions which the i4connected system requests from the external identity provider. For instance, the configured identity provider user email address. The Scopes array should be added between square brackets and each scope should be added between double-quotes. Lists which permissions should be requested.
UsePKCE - The Proof Key for Code Exchange allowing the user to prevent attacks and to be able to securely perform the OAuth exchange from public clients.
Make sure to save your changes to the appsettings.json file.
Next, connect to your i4connected database server, using either the Azure Data Studio or Microsoft SQL Server Manager Studio.
Open the Clients table and identify the JS Client in order to extract the ClientId. The default ClientId of the JS Client is 1.
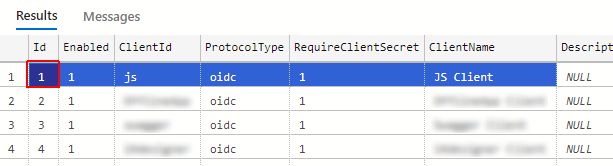
Open the ClientRedirectUris table and add the valid portal URL associated with the ClientId of the JS Client.
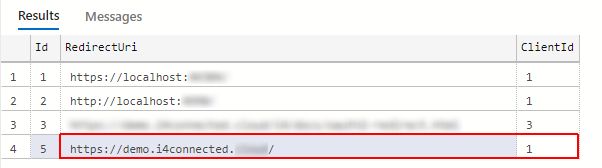
Open the ClientPostLogoutRedirectUris table and add the valid portal URL associated with the ClientID of the JS Client.
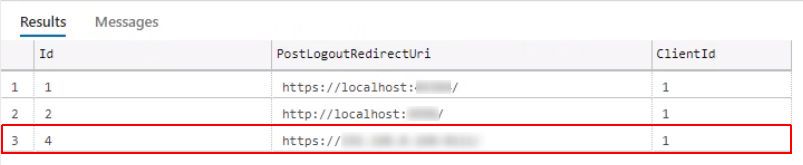
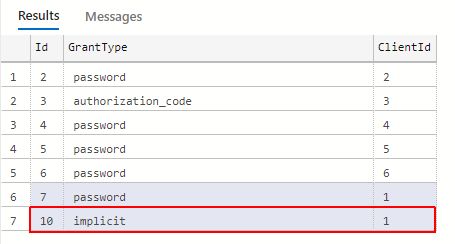
Next, open the ClientGrantTypes table and make sure that at least the GrantType Implicit is associated with the same ClientId.
Warning
To allow access to both External Providers Users and i4connected portal Users, you need to create associations of both "implicit" and "password" grant types for the same JS Client.
Make sure to save your changes to the Tables.
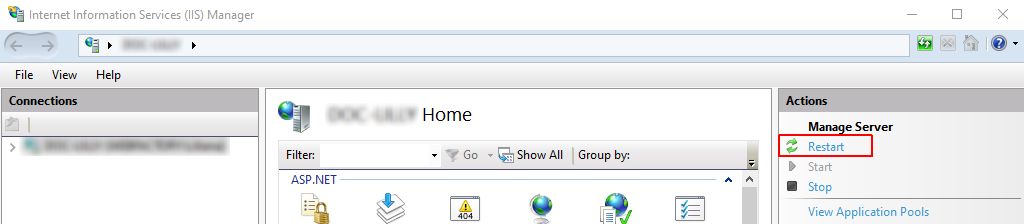
To apply the above settings, please make sure to Restart Internet Information Services (IIS).